Cloud Connectivity — Part II: Managed Network Access
The outsourcing of applications to the public cloud poses challenges to the communication between users and applications, but also between hybrid applications, such as data in the data center and web applications in the cloud.
From the workplace to the cloud
Cloud services can be obtained in a variety of ways. A typical access goes from the workplace of an employee and reaches the cloud service via x stations. The following list shows the positions involved:
- Local LAN (Wired/Wifi)
- Firewall
- Internet/WAN connection
- Internet/WAN Gateway
- Internet/WAN Public Cloud Provider
- Firewall Public Cloud Provider
- Local Public Cloud Provider Network
1.-2. is provided mostly by internal and partly also by external providers. The service level typically corresponds to the office hours of the own organisation.
3.-4. is usually "only" purchased. However, performance and SLA should be defined by the organization itself. For example, you should be aware of what the maximum downtime of a line may be.
5.-7. is part of the cloud package offered by the public cloud provider.
The list shows that a cloud connection involves a wide variety of parties and service providers. As the number of parties grows, the operation of such a "cloud connection" can soon become complicated. By using a "Managed Network Access" service, security aspects can be addressed in addition to optimum technical performance.
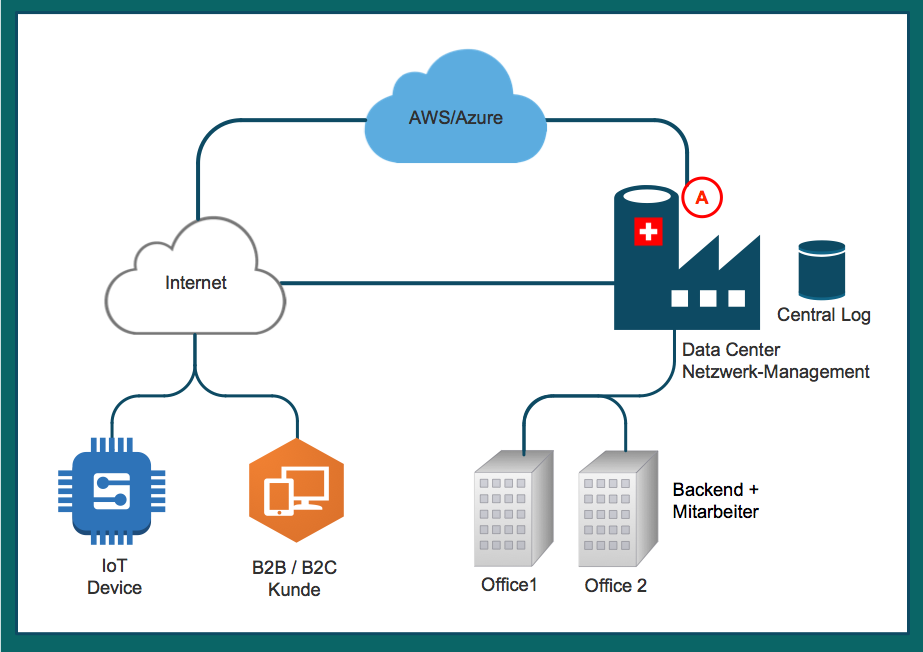
Blue Print «Managed Network Access»
Within the company's premises are the office workstations and, if necessary, a backend service or test systems. The first, and at the same time the last, mile is provided by a carrier based in the same country. It makes sense to choose a carrier that has access points to the Internet and a cloud provider. However, these access points (A) are not to be found in all data centres located in Switzerland.
The data centre may contain outsourced applications and data that have to be operated in the home country to meet security or data protection requirements, for example.
The transition point between "carrier of the last mile" and the applications in the data center lies ideally inside the company and not over Internet exchange points or even through the Internet.
Ideally, the service provider has powerful Internet connections so that access for IoT components, remote workstations as well as B2C and B2B partners can be guaranteed via these and the data center infrastructure. In addition, service providers usually have private peerings with the most important carriers and major users such as the SBB or major banks. Likewise, all logs of all systems involved such as routers, VPN, remote access and other services are stored in the data center. This means that all access logs can be archived independently of the cloud and your own four walls in a way that complies with auditing requirements.
There are several possible ways from the data center to the cloud. Larger service providers have both private lines and private peering on the local Internet exchange nodes (in Switzerland: SwissIX) to the large public clouds such as Azure and AWS.
But even an optimally configured line data center and Internet connection architecture does not guarantee optimal security. It is therefore advisable to establish a managed VPN service in your environment independently of the line and cloud service providers. In order to avoid a vendor lock-in by a cloud provider, for example, it is advisable to purchase software or a managed service that operates independently of the cloud.
In conjunction with Cyberlink and Aviatrix, Aspectra offers end-to-end "Managed Network Access", from local workstations over Swiss data centers to public clouds. Its components include local connections, cross-location VPN connections, monitoring of all relevant services and central log collection of all involved system components.
Further information:

